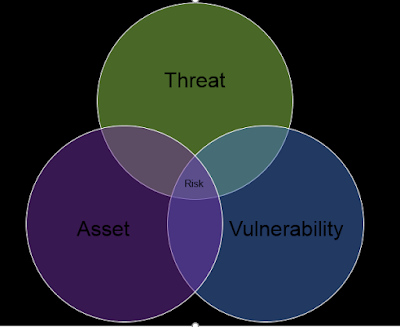
Now we are in the threat analysis stage, which means that we have to use the resources we identified earlier in the process to enumerate the business assets, their vulnerabilities, the imposing threats and threat types, and assess the risk to the environment. While there are many ways to demonstrate the relationship between all four elements, a simple Venn diagram seems to illustrate this nicely:
While this assignment proved to be a lot of work researching the material, it was also probably the most rewarding. I was very impressed by the pot of gold I found in NIST's National Vulnerability Database by using just a few keywords that applied to the case study. However, this is only a repository for hardware, firmware, or software weaknesses. Since processes are usually unique to an organization, finding process vulnerabilities will require a supplemental assessment.
No comments:
Post a Comment