The Threat from Computer Hacker Groups will Increase
“Computer hacker groups will continue to emerge in developing countries around the world, increasing the threat of malicious attacks motivated by religion, politics, and money”
The prediction that the threat from computer hacker groups will increase refers to the number and strength of attacks we will see in the near future because of the growing use of the Internet in developed countries. As more people start using the Internet to feed their special interests, the hacker subculture also advances in numbers and abilities as they continue to share information, techniques, tools, and common objectives.
Pierluigi Paganini, Chief Information Security Officer at Bit4Id, has outlined his predictions in relation to cybersecurity for 2016 and 2017. All of his predictions for 2016 have been fulfilled, including Cyber espionage will be the most serious threat to governments and private businesses, stating “nation-state actors have continued to represent one of the main threats to government and private businesses. In the last twelve months, the number of cyber-attacks aiming to steal sensitive information and intellectual property continued to increase.” Nation-state actors fall into the computer hacker group category with a political motivation, as they are typically hired by their government to carry out espionage, propaganda or outright sabotage through the use of hacking techniques.
Paganini has also cast his predictions for 2017, including Nation State Actors hacking and the urgency of norms of state behavior. This prediction builds on last year’s, but surmises that the detection abilities will also increase, exposing more hacking agendas.
We will be able to watch how this prediction plays out by evaluating attacks by origin, type, and target at http://map.norsecorp.com/#/. This map is a live feed of a threat intelligence network, and while it doesn’t specifically show the motivation for the attacks, we can use the data to speculate motivations based on the current state of affairs within and between borders.
What are your observations for 2017 so far?
References
Norse Corp. (n.d.). Norse Attack Map. Retrieved August 29, 2017, from http://map.norsecorp.com/#/
Paganini, P. (2016, December 18). 2017 Cyber Security Predictions. Retrieved August 29, 2017, from http://resources.infosecinstitute.com/2017-cyber-security-predictions/#gref
Taylor, R. W., Fritsch, E. J., & Liederbach, J. (2015). Digital Crime and Terrorism. In Digital crime and digital terrorism (pp. 355-356). Upper Saddle River, NJ: Pearson/Prentice Hall.
Tuesday, August 29, 2017
Monday, May 29, 2017
CYBR 650 Week 12 – What is cybersecurity?

This seems a little counter intuitive, but I want to address the topic of what cybersecurity really is as my final post in this class.
When the topic of cybersecurity comes up in conversations, there tends to be some confusion as to what it entails. While knowledge about networking is crucial to be successful in cybersecurity, it is only one piece of the puzzle.
When the topic of cybersecurity comes up in conversations, there tends to be some confusion as to what it entails. While knowledge about networking is crucial to be successful in cybersecurity, it is only one piece of the puzzle.
I started the cybersecurity program with a background in information management. I chose cybersecurity because it is a specialized area of information management, and I loved working with the tools and methodologies. I have family that worked in law enforcement, so I guess you could say I am continuing the family business, albeit in a different environment. Cybersecurity professionals have different types of skill sets, just like any other field. Diversity is the key to having a successful team, and cybersecurity is no different.
As I complete the final phase of my education, I am better equipped to articulate my thoughts and proficiencies in all areas of cybersecurity. In addition to networking, this includes social
engineering, computer forensics, physical security, threat modeling,
risk management, disaster recovery, etc. The list is endless, and those were only the high-level
takeaways.
I am excited to go forth and make an impression in the cybersecurity field.
I am excited to go forth and make an impression in the cybersecurity field.
Sunday, May 21, 2017
CYBR 650 Week 10 – Security Tools
In week two, we identified credible sources of information for our threat process model. What about tools? There are hundreds of security tools available, so how do we determine which ones to use?
Fortunately, Offensive Security developed Kali Linux in response to this need. Kali is a security distribution of Linux aimed at penetration testing, but it offers so much more. While there are too many tools to go into detail, a complete listing of tools is available at http://tools.kali.org/tools-listing under the following categories:
If you are a fan of Linux, you will not be disappointed. I had installed its predecessor BackTrack a few years ago, and have been hooked since. Which tools are your favorites? Please leave your comments below.
Fortunately, Offensive Security developed Kali Linux in response to this need. Kali is a security distribution of Linux aimed at penetration testing, but it offers so much more. While there are too many tools to go into detail, a complete listing of tools is available at http://tools.kali.org/tools-listing under the following categories:

- Exploitation Tools
- Hardware Hacking
- Forensics Tools
- Information Gathering
- Maintaining Access
- Password Attacks
- Reporting Tools
- Reverse Engineering
- Sniffing & Spoofing
- Stress Testing
- Vulnerability Analysis
- Wireless Attacks
- Web Applications
If you are a fan of Linux, you will not be disappointed. I had installed its predecessor BackTrack a few years ago, and have been hooked since. Which tools are your favorites? Please leave your comments below.
Sunday, May 14, 2017
CYBR 650 Week 9 – Action Plan
As we progress through our threat models with the corresponding assignments, I have come to realize that we are only scratching the surface of threat modeling. The Harry and Mae's case study has so many unknown variables that would normally be addressed in a real environment, and consequently gets left out of the assignments. Some of the known variables are generic descriptions, and we have to make assumptions in order to give a proper analysis.
In any case, I feel threat modeling requires much more time to solicit information, document the environment, investigate specific threats and vulnerabilities, calculate the risks, provide more detailed recommendations, and identify metrics for defining success. As students (most of us with full-time jobs), we have limited time to completely cover all aspects, and I have noticed some scope shrinkage in order to demonstrate that we understand the basic concept of the assignments.
It seems that a comprehensive threat analysis would require a diverse team of security consultants working with the in-house network engineers, system admins, and project managers over a span of weeks to encompass everything that would benefit from a security makeover. As a result, I have a much deeper appreciation for the opportunity to learn this process, and for the experts who carry this out on a daily basis.
In any case, I feel threat modeling requires much more time to solicit information, document the environment, investigate specific threats and vulnerabilities, calculate the risks, provide more detailed recommendations, and identify metrics for defining success. As students (most of us with full-time jobs), we have limited time to completely cover all aspects, and I have noticed some scope shrinkage in order to demonstrate that we understand the basic concept of the assignments.
It seems that a comprehensive threat analysis would require a diverse team of security consultants working with the in-house network engineers, system admins, and project managers over a span of weeks to encompass everything that would benefit from a security makeover. As a result, I have a much deeper appreciation for the opportunity to learn this process, and for the experts who carry this out on a daily basis.
Sunday, April 30, 2017
CYBR 650 Week 7 – Threat Analysis
This week has been a bit of a challenge in class, as we apply our threat models to a case study. So far, we have created our own threat process models, identified credible sources to stay current, and analyzed the fictitious system in the case study.
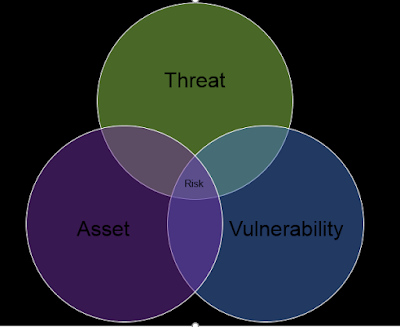
Now we are in the threat analysis stage, which means that we have to use the resources we identified earlier in the process to enumerate the business assets, their vulnerabilities, the imposing threats and threat types, and assess the risk to the environment. While there are many ways to demonstrate the relationship between all four elements, a simple Venn diagram seems to illustrate this nicely:
Now we are in the threat analysis stage, which means that we have to use the resources we identified earlier in the process to enumerate the business assets, their vulnerabilities, the imposing threats and threat types, and assess the risk to the environment. While there are many ways to demonstrate the relationship between all four elements, a simple Venn diagram seems to illustrate this nicely:
While this assignment proved to be a lot of work researching the material, it was also probably the most rewarding. I was very impressed by the pot of gold I found in NIST's National Vulnerability Database by using just a few keywords that applied to the case study. However, this is only a repository for hardware, firmware, or software weaknesses. Since processes are usually unique to an organization, finding process vulnerabilities will require a supplemental assessment.
Saturday, April 22, 2017
CYBR 650 Week 6 – Women in IT Security
This week I had the privilege of attending the annual ICAN Women's Leadership Conference. The theme this year focused on women balancing work and life, which has been a decades-long struggle while we are still trying to break out of traditional gender roles.
Michael Kimmel, Professor of Sociology & Gender Studies at Stony Brook University, gave one of the most interesting key note presentations on the main stage: The Gendered Society. He stated, "Research by Catalyst and others has shown conclusively that the more gender-equal companies are, the better it is for workers, the happier their labor force is. They have lower job turnover. They have lower levels of attrition. They have an easier time recruiting. They have higher rates of retention, higher job satisfaction, higher rates of productivity."
What does this mean for cybersecurity? Kimmel pondered why there are so few women at the top of STEM careers. His theory is that due to the expectations placed on women within the home, many women are simply unable or unwilling to dedicate the time and effort it takes to advance in a male dominated field. The statistics for women in cybersecurity are staggering:
So what needs to be done to level the playing field? Please leave your comments below.
You can also watch one of Professor Kimmel's recent presentations at: https://www.ted.com/talks/michael_kimmel_why_gender_equality_is_good_for_everyone_men_included
Friday, April 14, 2017
CYBR 650 Week 5 - TechJunction 2016
I recently had the opportunity to be on the advisory committee for TechJuncion 2016, a technology conference geared towards security and server management. It is hosted annually right here in the heartland of America, and the best part is that it's free to attend! Here are some of the highlights:
Passwords Suck: A Platform Approach To Securing Enterprise Identities
Presented by: Centrify
This presentation advocated single sign-on software. Statistics for password theft show that 63% of breaches were due to compromised accounts.
Ransomware: All Locked Up With No Place To Go
Presented by: Kaspersky Lab
Kaspersky Labs outlined how businesses can protect themselves against ransomware through backups, updates, and anti-virus programs. Kaspersky offers System Watcher and Automatic Exploit Prevention as security tools to prevent against ransomware. Current statistics of ransomware are available in Verizon'€™s 2016 Data Breach Investigations Report - see below for the link.
Defending Against Modern Malware
Presented by: WatchGuard Technologies, Inc.
WatchGuard delivered a sobering speech about modern malware. They stated that modern malware is moving from signatures to binary patterns. For example, ransomware uses bitcoins for payment, and is almost impossible to track. They also identified three different cyber attacker profiles: Hacktivist, Cyber Criminal, and Nation State. The good news is there are websites that monitor attacks and breaches (see Other Websites section below), and WatchGuard has designed a solution to break the Cyber Kill Chain (see their PDF presentation below).
Why Do You Need DR?
Presented by: Zerto, Inc.
Zerto started the presentation by pointing out that disasters are both natural and operational. Disaster recovery planning should include backup, redundancy, impact/urgency considerations, and should turn a disaster into a non-event.
Innovation Matters
Presented by: SimpliVity
Simplivity defined innovation as a means to improve on a service based on current needs. They used Netflix as an example of how they capitalized on Blockbuster's current movie rental service by catering to current and future business trends, and changing the way the service is delivered.
Hyperconvergence is today's way of innovating by combining several functions into one delivery method. An example of hyperconvergence is how phones evolved from just a device to make calls, to smart phones, which can browse the web, track fitness goals, display the current weather, and so much more. Hyperconvergence allows us to virtualize server, data, network resources to optimize delivery and reduce duplication.
Keynote Presentation: Surviving Security Groundhog Day
Presented by Ron Woerner • Director & Professor, Cybersecurity Studies at Bellevue University
This speaker deserves special accolades, as he has been the driving force behind my pursuit of a Master's degree in Cybersecurity. Prof. Woerner indicated that technology has advanced to IoT (Internet of Things), but security isn't getting any better. Humans are still the weakest link, and complacency is a big culprit. He reassured the attendees that security never has to be 100%, just good enough, but you need to have an iron-clad contract for cloud services to be secure. His motto: If you SEE something, SAY something!
Thanks for all you do, Coach.
Resources
Verizon 2016 Data Breach Investigations Report
http://www.verizonenterprise.com/verizon-insights-lab/dbir/2016/
IT Policy Compliance for Dummies
https://www.qualys.com/dummy-pc
PCI Compliance for Dummies
https://www.qualys.com/dummy-pci
Web Application Security for Dummies
https://www.qualys.com/dummy-was
Vulnerability Management for Dummies
https://www.qu alys.com/dummy-vm
Other Websites:
Data Visualizations (Ex: data breaches)
http://www.informationisbeautiful.net/
Malc0de Database - an updated database of domains hosting malicious executables
http://malc0de.com/database/
Norse - an interactive map of attacks
http://map.norsecorp.com/
WatchGuard Presentation
http://schd.ws/hosted_files/trivalentgroupsolutionsexpo2015/5b/WatchGuard-%20Defending%20against%20Modern%20Day%20Malware.pdf
Subscribe to:
Posts (Atom)